Microsoft Entra ID SSO for Proxmox
Prerequisites: Ability to create an app registration with delegated standard rights. Proxmox should be installed and access to the Datacenters Realms section should be possible.
Proxmox allows various external authentication services via protocols such as Active Directory, LDAP or OpenID Connect. We will use the latter for the Microsoft Entra ID connection and SSO functionality.
Limitations
Proxmox allows the automatic creation of user objects, but is otherwise relatively limited compared to other applications, as it does not use the OAUTH 2.0 standard but only handles logins via Open ID Connect. These certain limitations must be taken into account when introducing this setup.
In addition, logins will only be possible for the Webgui. The login on the individual cluster nodes is still regulated via the Linux authentication of the individual hosts. This means that no console connections can be made to the host shells with the Microsoft Entra ID user objects.
Create App Registration
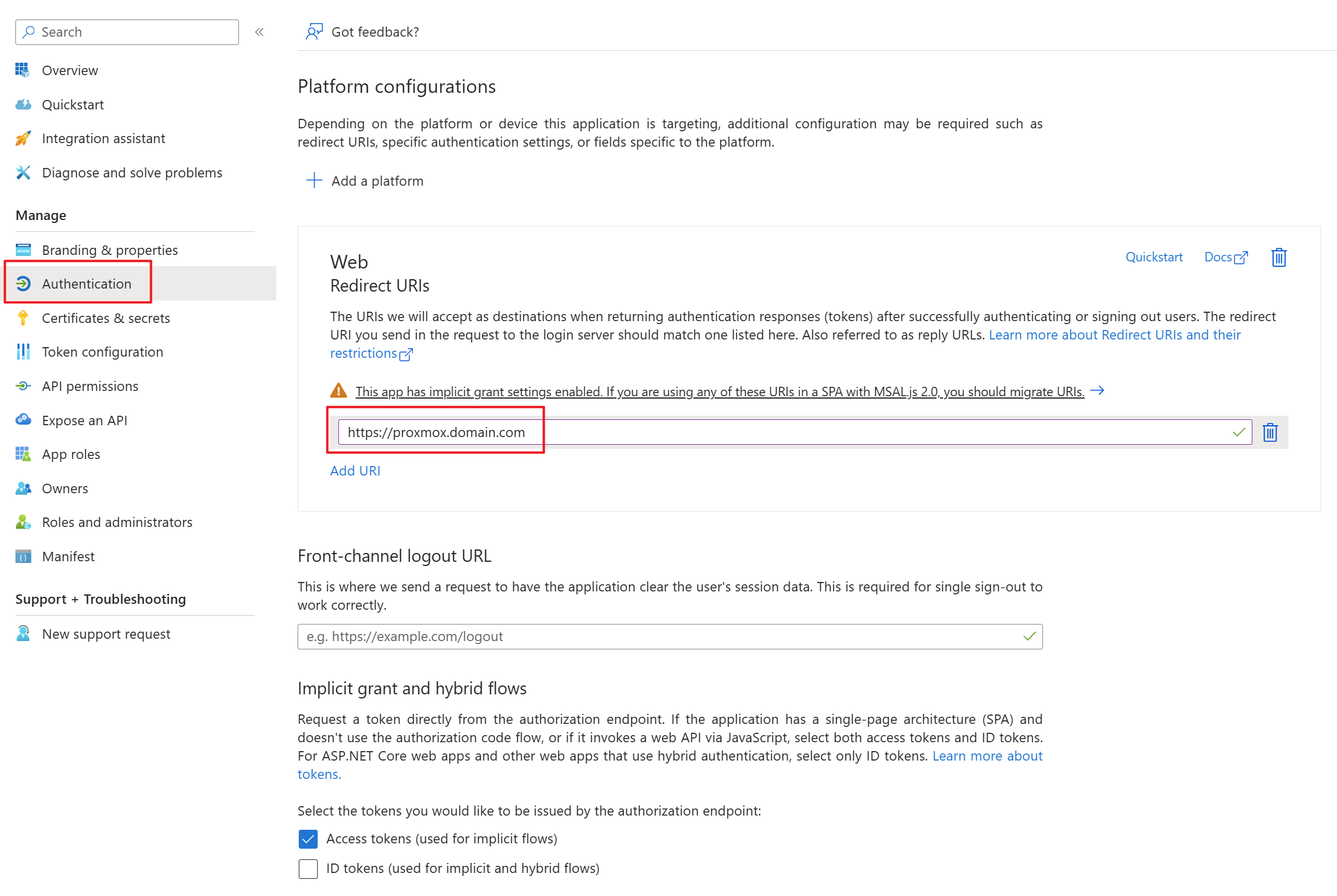
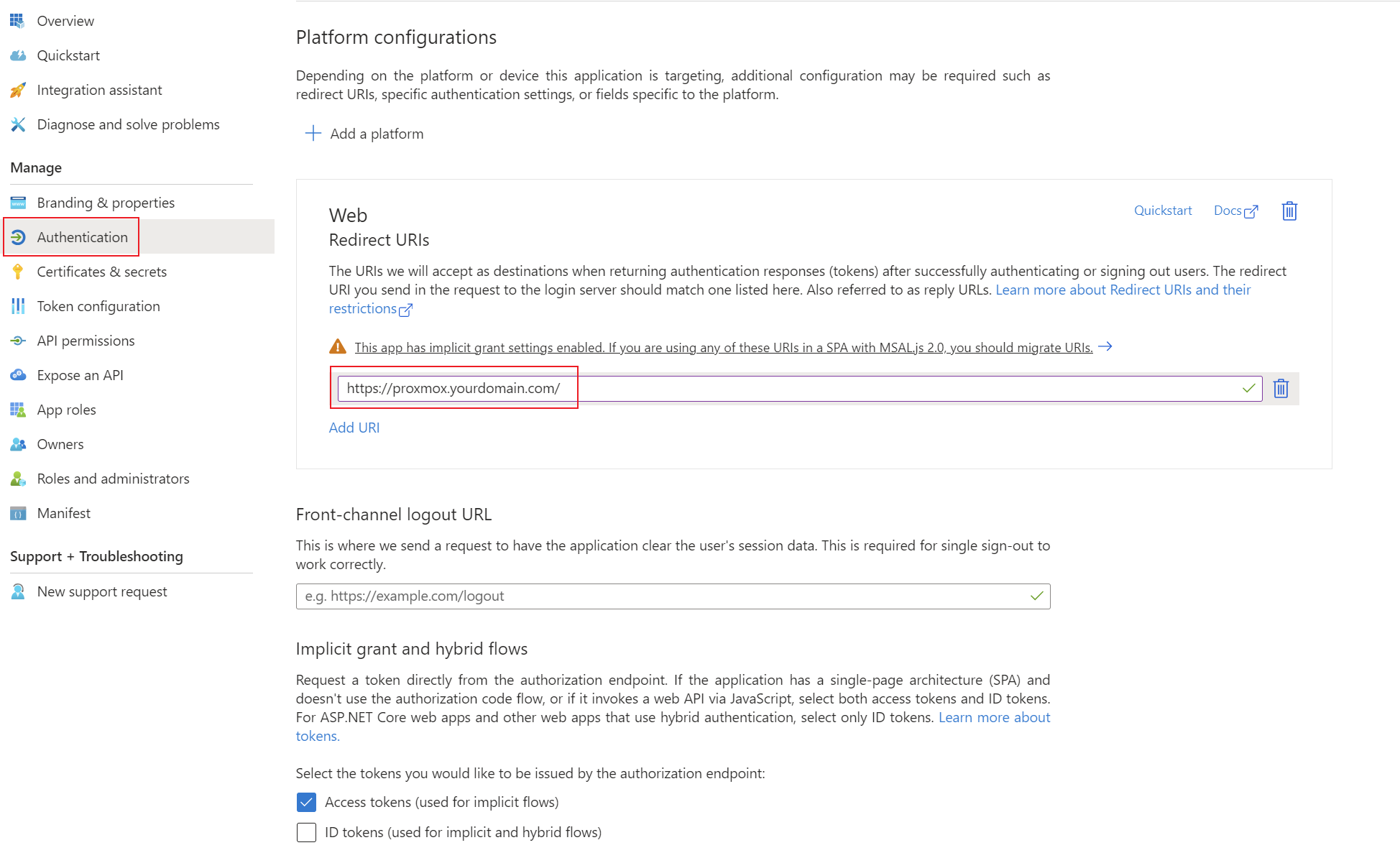
First, an app registration including client secret must be created in Microsoft Entra ID. All settings can be left at the default values. TheImportant only important settingsettings are the Redirect URIs under the Authentication tab. Set these URIs to your external or internal domain on which Proxmox is available. These URIs will be used for Microsoft Entra ID to know where to redirect the user in case of successful logins.
- Authentication Type: Web
- Redirect URIs: https://proxmox.yourdomain.com/
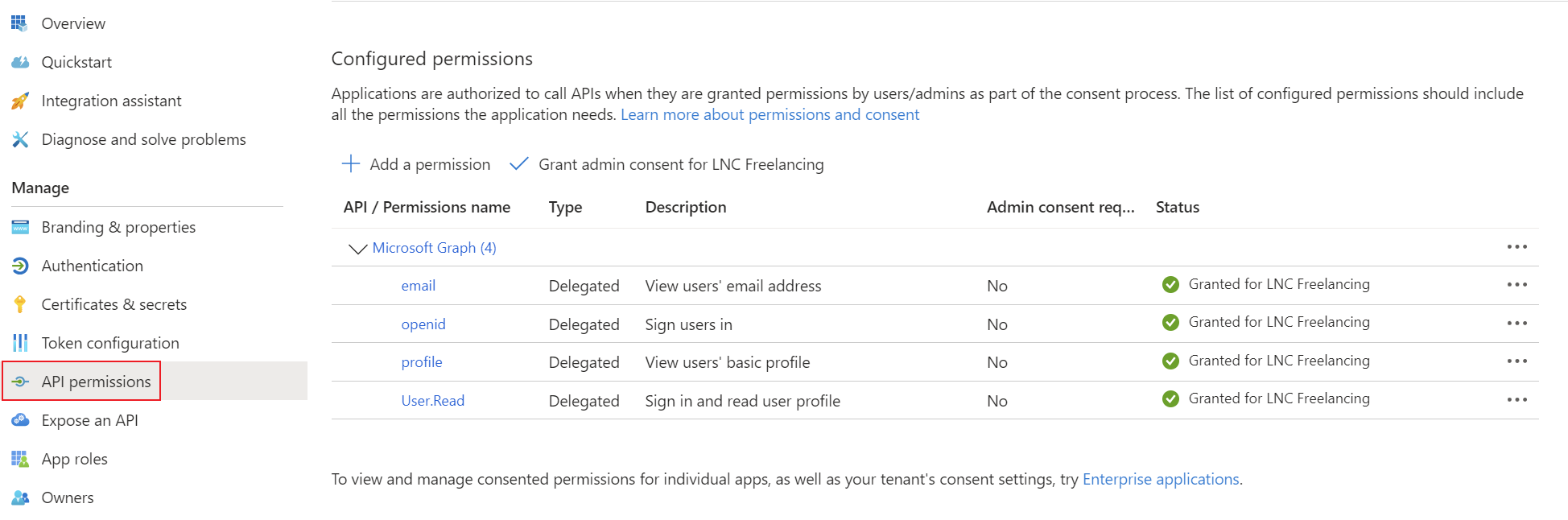
Add the corresponding permissions for OpenID Connect as delegated permissions and grant admin consent for your tenant.
- Permissions: Delegated OpenId permissions (email, offline_access, openid, profile)
Create a client secret for the application and save the tenant ID, application ID and client secret in your password manager. You can find instructions for this information here: Get app details and grant permissions to app registration
Setup Microsoft Entra ID in Proxmox Realm
This step requires the authentication details TenantID, ClientID, Client Secret from the first step.
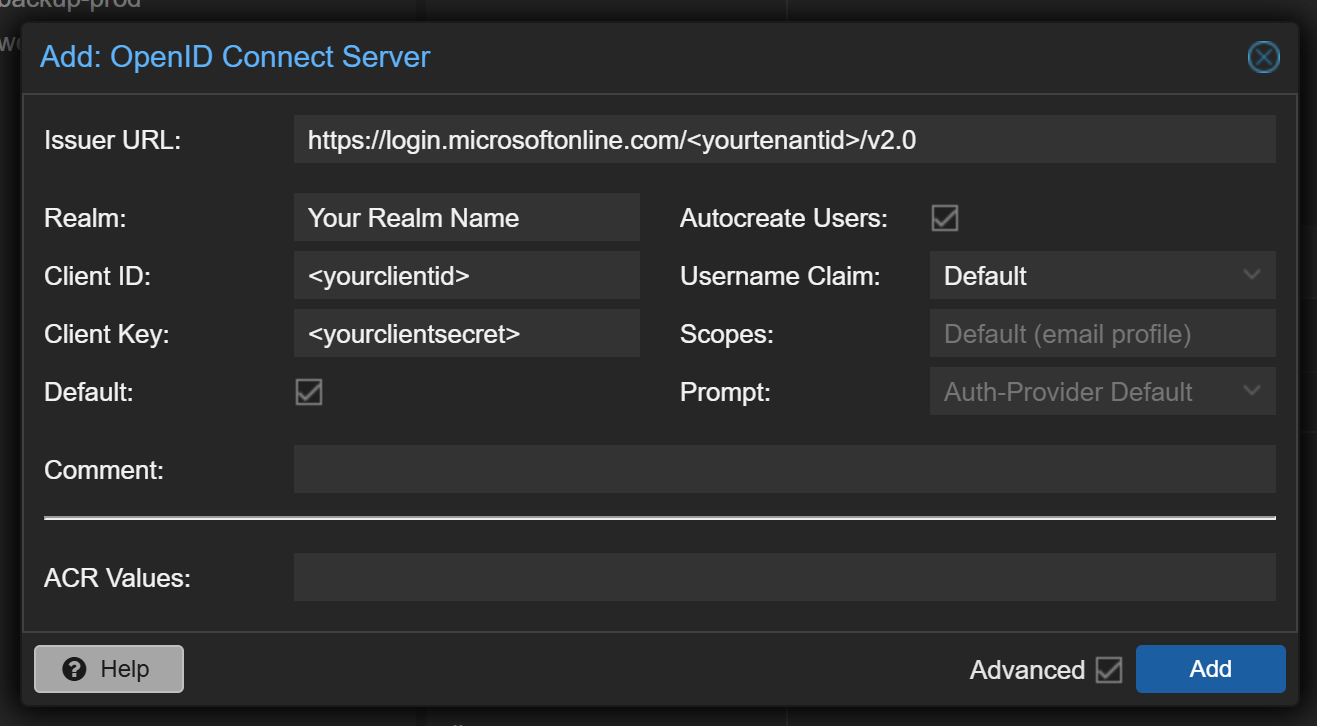
In the Proxmox web interface select "Datacenter" -> "Realms" -> "Add" -> "OpenID Connect Server". There you can enter the credentials from Microsoft Entra ID. Enter the information as described here: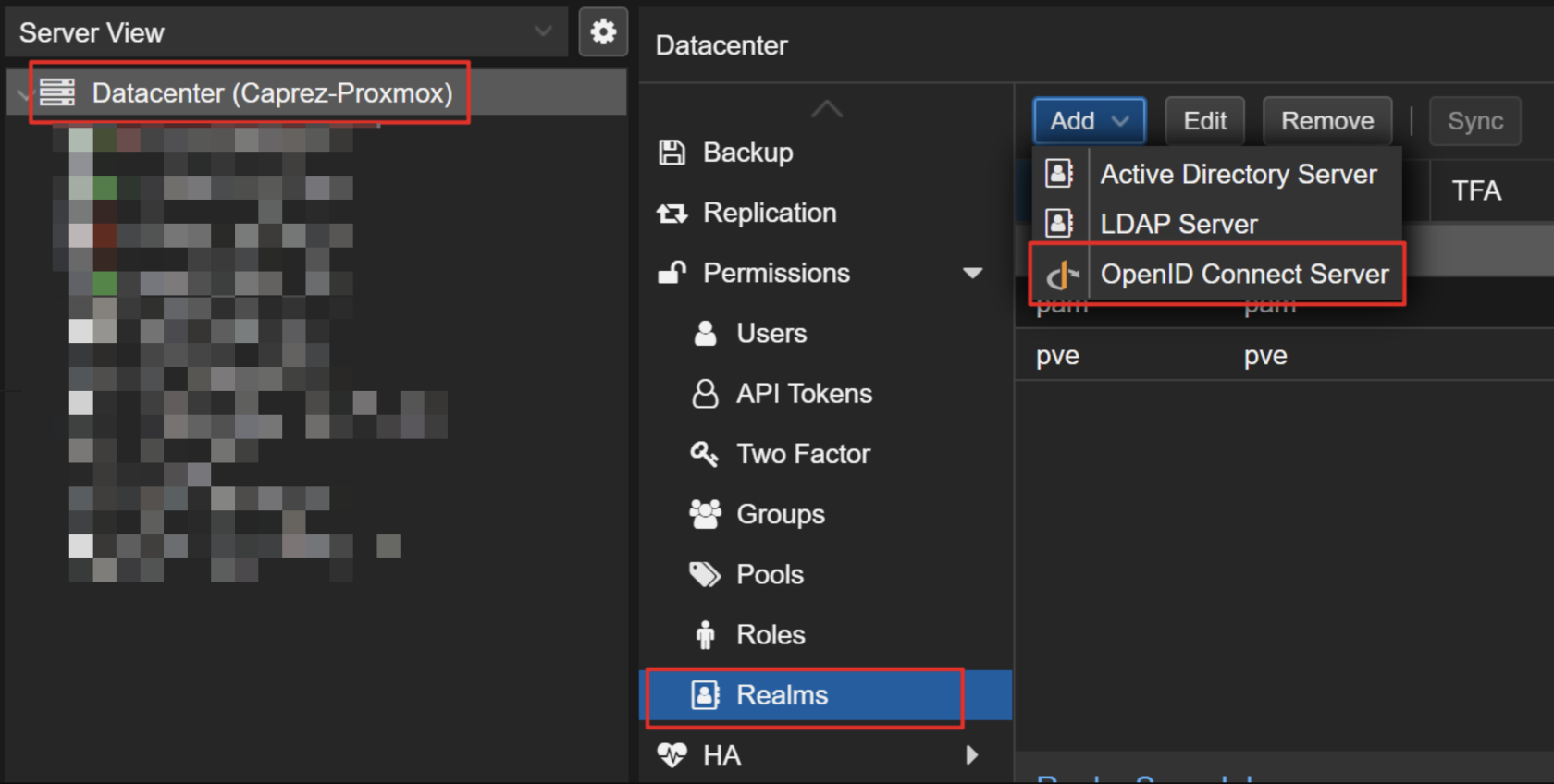
- Issuer URL: https://login.microsoftonline.com/<yourtenantid>/v2.0
- Realm: This is the id of the installed authentication provider. The name must be lower case and without special characters.
- Client ID: Enter your ClientID from the App Registration of your Microsoft Entra ID.
- Client Key: Here you have to enter the Client Secret.
- Default: If this box is checked, the default auth provider on the sign in screen will be this method.
- Autocreate Users: If this is enabled all user who have permission to sign in to your App Registration, are automatically signed up as user objects in Proxmox. As you can still manage permissions within the App Registration this is usually recommended.
- Scopes: This allows you to receive multiple parameters from the Microsoft Entra ID user object. The Access Token is requested with these scopes at login. The default values are usually sufficient.
- Prompt: This setting defines which action Proxmox should perform when users log in. The default options are sufficient for the Microsoft Entra ID login.
- Comment: Enter a name that will be displayed to the end user on the login screen in the auth provider selection.
After these settings are properly configured your users should be able to sign into Proxmox web interface. After sign in the default grouping, role and permissions mechanisms from Proxmox take place.