Credential handling with Azure KeyVault
With this option, the secrets for Azure Functions are stored in an Azure Key Vault. An access policy is placed on the Key Vault which only allows the Managed Identity of an Azure Function to read the secret. On the Azure Function side, a Managed Identity is set up as well as an Environment Variable that is linked to the Secret in the Key Vault.
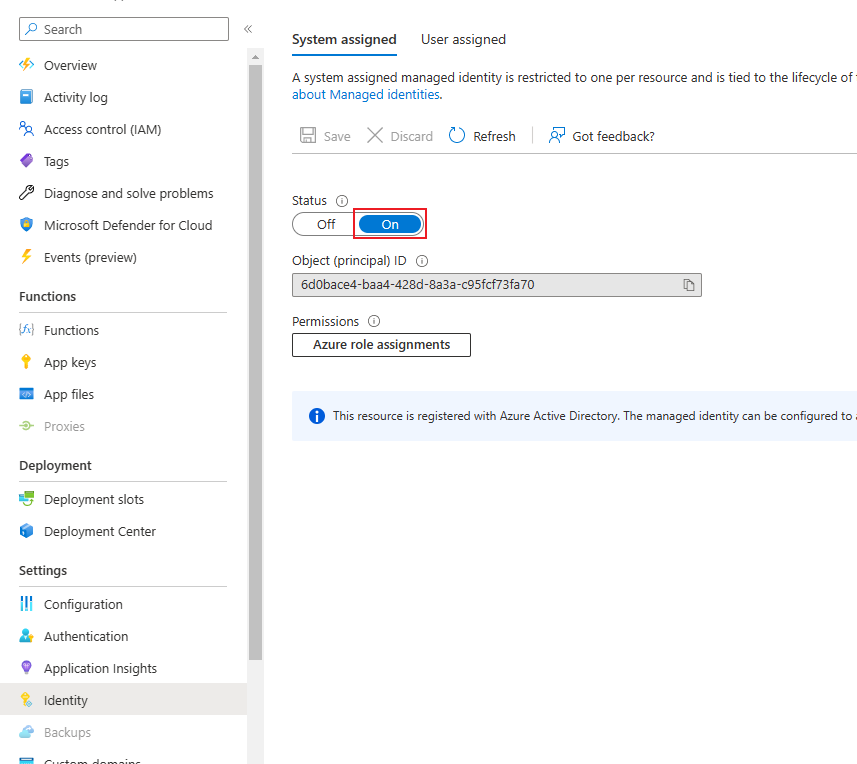
Activate managed identity
To authenticate against the Key Vault you can activate the Managed Identity of your Function App. Thus, permissions can be given to the function app and used within the function.
Create new Key Vault Secret
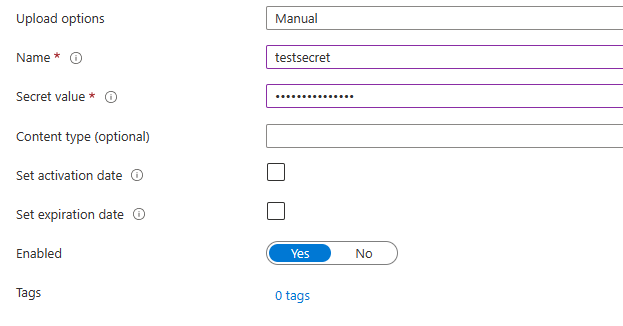
Create a new secret in the key vault and give this secret a unique name. This name will then be used to create a link from the Function App Variable to the Key Vault.
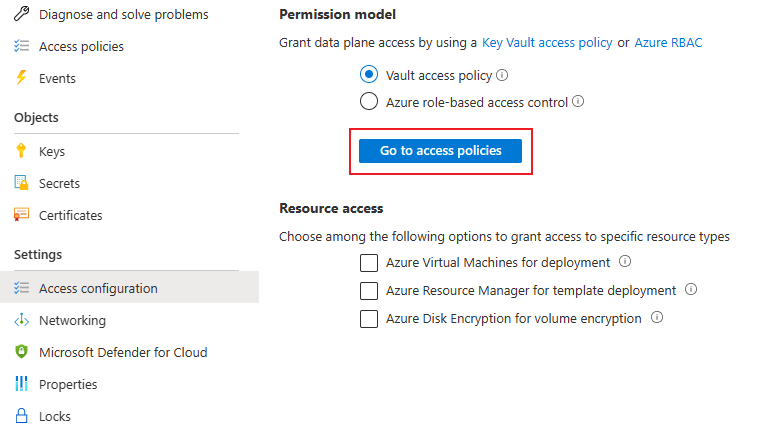
Activate access policies
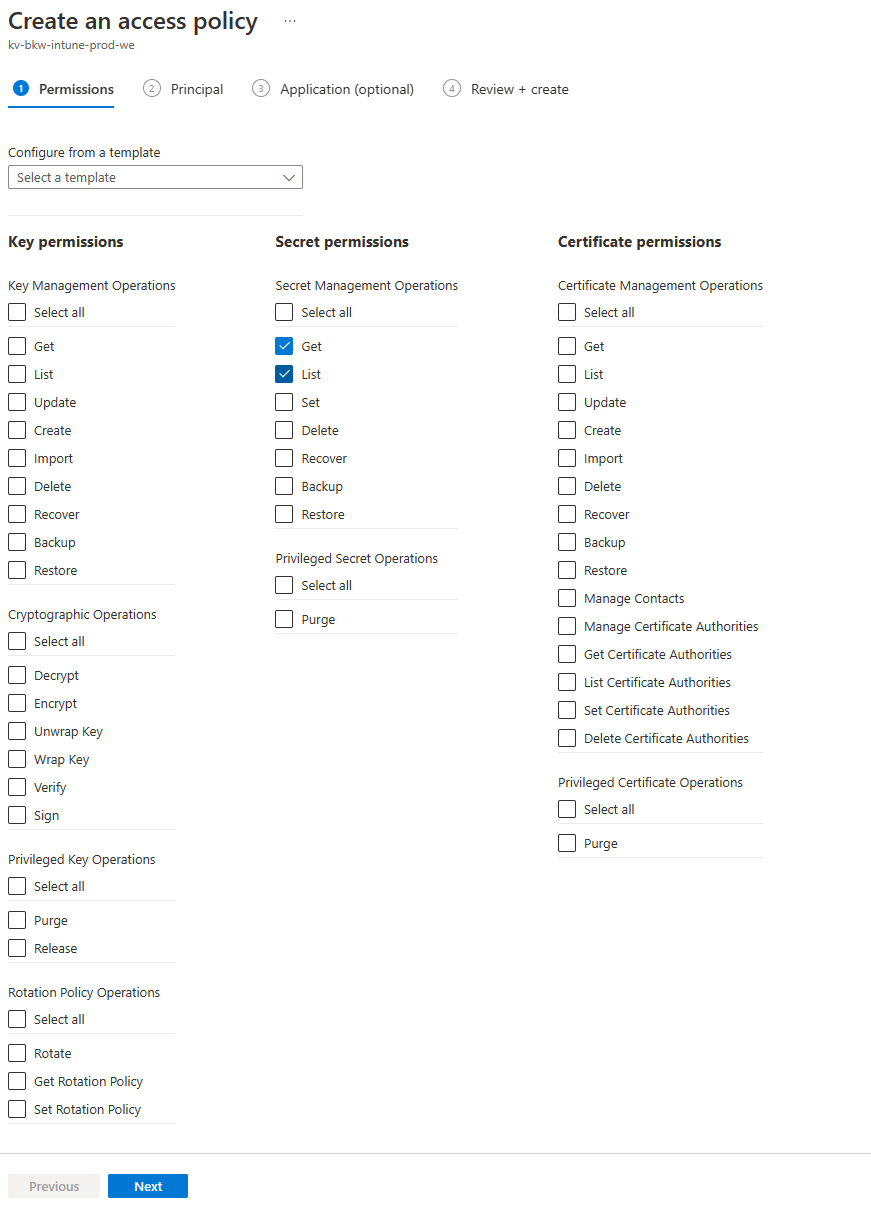
Go to access policies to create a new permission container for the Azure Function.
Select the necessary permissions for your function app.
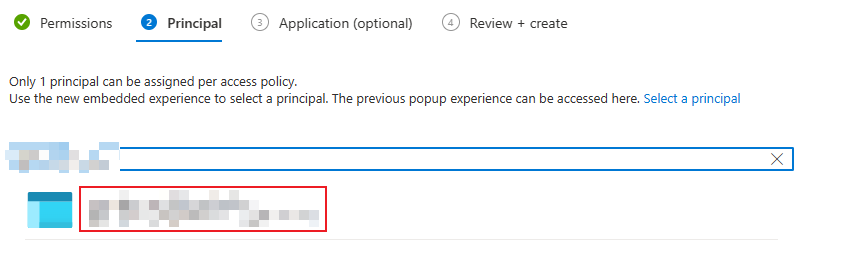
Select the appropriate Managed Identity from the function, which was created earlier.
Add environment variable link
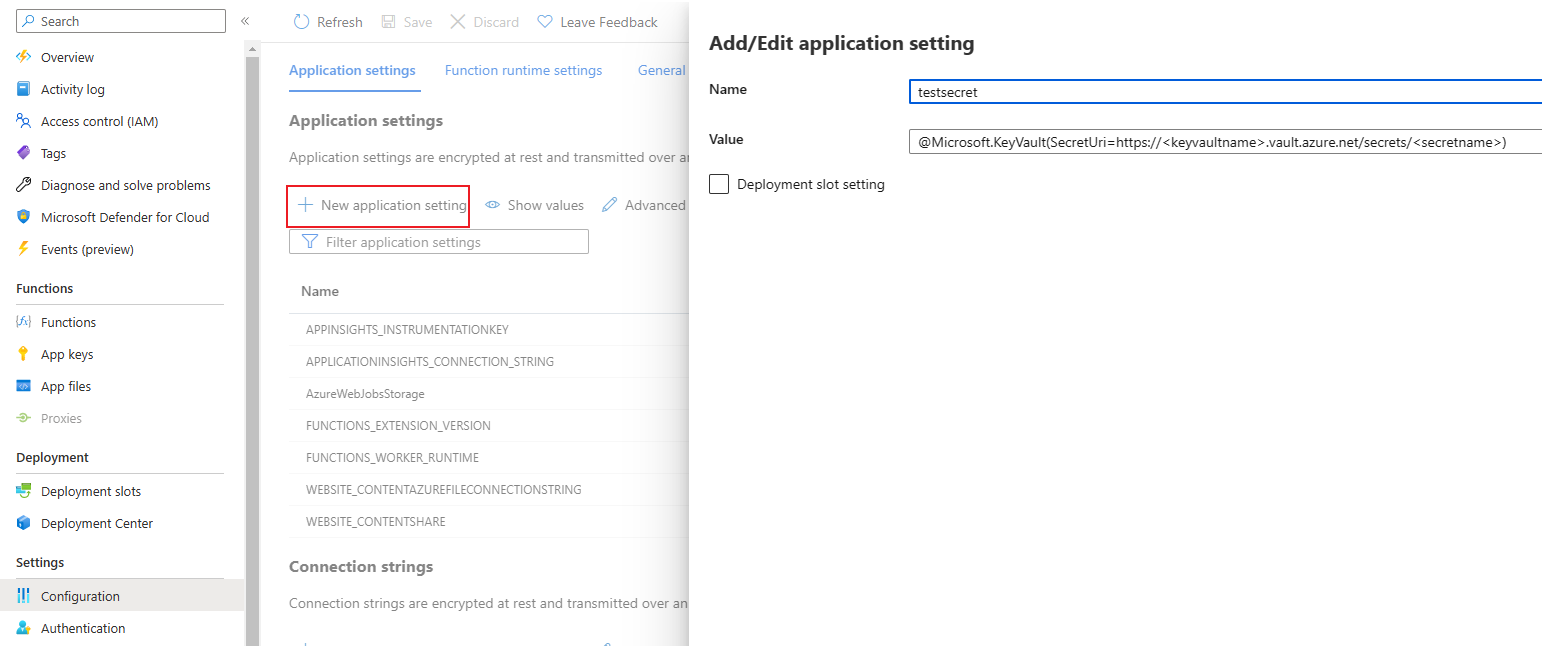
Then you can get the Key Vault name and secret name. With this information you can create an Application setting which will create an environment variable to use in the Azure Functions code. Set the name of the Environment Variable and create a link to the corresponding secret in the Key Vault.
@Microsoft.KeyVault(SecretUri=https://<keyvaultname>.vault.azure.net/secrets/<secretname>)
Usage in function code
When everything is implemented as described you can use the variable accordingly:
$testsecret = $env:testsecret